Imagine this: You’re feverishly coding a new app, debugging a website, or running a local server. In your terminal window or log file, flashes a cryptic message: 127.0.0.1:62893. It looks like gibberish, maybe even slightly alarming. Is it a hacker? A system error? Relax. This isn’t an intruder knocking; it’s your computer having a quiet, essential conversation with itself. That string, especially that seemingly random port number like 62893, is the digital equivalent of your machine whispering notes in its own private diary. Let’s pull back the curtain on this fundamental, yet often overlooked, piece of tech magic.
Why Your Computer Needs to Talk to Itself (And How It Does It)
Think of localhost or its numerical address 127.0.0.1 as your computer’s internal “home address.” It’s not reachable from the outside internet; it’s purely for internal communication. Just like different services in a building (mailroom, cafeteria, offices) need unique room numbers, software components on your computer need unique identifiers to send and receive data. This is where ports come in.
- 127.0.0.1: The unchanging loopback address. Always points back to this machine.
- :62893: The dynamic port number. Think of this as a temporary meeting room assigned by your operating system for a specific, short-lived conversation.
The Unsung Hero: Dynamic Ports Explained
Ports range from 0 to 65535. The lower numbers (0-1023) are “well-known ports” reserved for standard services (like port 80 for HTTP web traffic, port 443 for HTTPS). Ports 1024 to 49151 are “registered ports” for specific applications. Ports 49152 to 65535 are the dynamic or private ports. This is where 62893 lives.
Here’s why dynamic ports are crucial:
- Avoiding Collisions: If every application tried to use the same popular port (like 8080 for alternative web servers), chaos would ensue. Dynamic ports ensure each new connection gets a unique identifier during its session.
- Ephemeral Nature: These ports are leased temporarily. Once the communication session ends (e.g., you close your local development server, a background process finishes its task), the port number
62893is released back into the pool. Next time something needs to talk internally, it might get54211or60984. - Security (Local Scope): Because these ports are used for
127.0.0.1traffic, the communication is inherently confined to your local machine. External entities cannot directly access services only listening on127.0.0.1:some_dynamic_portunless you explicitly configure complex tunneling or forwarding (which introduces its own risks).
Where You’ll Encounter 127.0.0.1:62893 (And Friends)
This pattern isn’t rare; it’s fundamental to how modern computing works locally:
- Software Development & Testing (The MVP): This is the most common scenario. When you run a web server (like Apache, Nginx, Node.js, Django’s development server) locally, it binds to
127.0.0.1on a specific port (sometimes you set it, like:8000, sometimes it’s dynamic). Your web browser, acting as the client, connects to that server usinglocalhost:8000or127.0.0.1:8000. Crucially, the browser itself uses a dynamic port like62893as its outgoing port for that connection. You’ll see127.0.0.1:62893in server logs indicating the browser’s connection origin.- Developer Scenario: You start your app server on
127.0.0.1:3000. You open Chrome and go tohttp://localhost:3000. Chrome uses a dynamic port (e.g.,62893) to connect to port3000. The server log shows:Connected from 127.0.0.1:62893.
- Developer Scenario: You start your app server on
- Database Connections: Local databases (MySQL, PostgreSQL, MongoDB) often run on
127.0.0.1. Applications connecting to them (like your Python script or Java app) will use a dynamic port as their source port when talking to the database’s fixed port (e.g.,3306for MySQL). - Inter-Process Communication (IPC): Different applications or services running on the same machine often need to exchange data. They might set up temporary communication channels using
127.0.0.1and dynamically assigned ports. - Docker Containers: Containers frequently communicate with the host machine (
127.0.0.1from the container’s perspective) or with other containers on the same host via internal networks, utilizing dynamic ports extensively for these connections.
Visualizing the Localhost Conversation
Let’s break down a typical interaction involving a dynamic port:
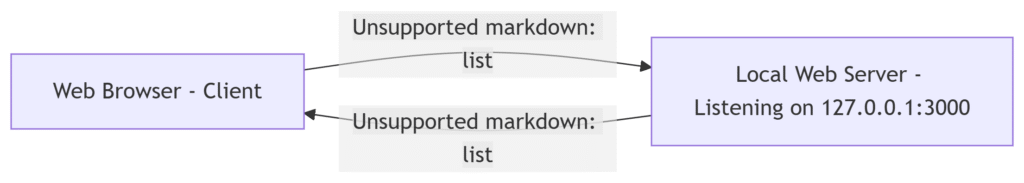
1. Browser (Client): “I need data from the server at 127.0.0.1:3000. My OS gave me outgoing port 62893 for this chat.”
2. Server: “I see a connection request coming from 127.0.0.1:62893 wanting my service on port 3000. Connection accepted. Sending data back to 127.0.0.1:62893.”
3. Browser: “Received data on my port 62893! Displaying it now.”
Dynamic vs. Well-Known Ports: A Quick Comparison
| Feature | Dynamic Ports (e.g., 62893) | Well-Known Ports (e.g., 80, 443) |
|---|---|---|
| Range | 49152 – 65535 | 0 – 1023 |
| Purpose | Temporary client connections | Permanent server services |
| Assignment | Automatically by the OS (Client-side) | Pre-defined by IANA (Server-side) |
| Stability | Ephemeral (Changes per connection/session) | Static (Always used for the same service) |
| Example Use | Browser connecting to local server | Web server listening for HTTP requests |
| Visibility | Often seen in logs as client source ports | Seen in URLs/configs as service address |
Security Implications: Should You Worry About 127.0.0.1:62893?
Seeing 127.0.0.1:62893 in logs is almost always benign and expected. It signifies normal internal communication. However, understanding its context is key for security hygiene:
- Malware Potential (Rare but Possible): Sophisticated malware could use localhost communication to evade network-based detection, passing data between malicious components running on the same machine using dynamic ports. Seeing unknown processes constantly communicating via
127.0.0.1on random high ports could be a red flag warranting investigation. - Misconfiguration Risks: If a service accidentally binds to
0.0.0.0(all interfaces) on a dynamic port instead of127.0.0.1, it might become accessible from your network, creating an unintended security hole. Always explicitly bind services to127.0.0.1during development unless network access is required. - The Loopback Shield: The core security benefit is isolation. Services only bound to
127.0.0.1are invisible and inaccessible from other machines on your network or the internet. Using127.0.0.1:some_portis inherently safer than exposing a service on your machine’s real IP address.
Beyond the Basics: Advanced Localhost Use Cases
- Port Forwarding/Tunneling: Tools like SSH (
ssh -L 8080:localhost:80 remote-server) create secure tunnels. This allows you to access a service on a remote server (listening on itslocalhost:80) as if it were running on your local machine on127.0.0.1:8080. Your local connection to127.0.0.1:8080would use a dynamic port like62893. - Container Networking: Docker creates complex virtual networks. When you map a container port to the host (
-p 8080:80), accessing127.0.0.1:8080on your host machine routes traffic to the container’s port 80. The container’s internal processes also communicate via their ownlocalhostinterfaces and dynamic ports. - Mocking & Service Virtualization: Developers use tools (like WireMock, Mountebank) that run locally on
127.0.0.1and dynamic ports to simulate external APIs or services for isolated testing.
Troubleshooting the “localhost” Dialogue
Sometimes things go wrong. Here’s how 127.0.0.1:port issues manifest:
- “Connection Refused” / “Cannot Connect”: Usually means no service is actively listening on the specified
127.0.0.1:port. Check if your server/application actually started correctly and bound to the expected port and address (127.0.0.1, not0.0.0.0). - “Address Already in Use”: This means another process is already using that specific port (e.g.,
3000) on127.0.0.1. Find and stop the conflicting process, change your application’s port, or wait for the OS to fully release the port. - Firewall Blocking Loopback? (Unlikely but Possible): Modern OS firewalls generally allow
127.0.0.1traffic by default. If you suspect firewall issues, temporarily disable it (for testing only!) to see if it resolves the connection problem. Crucially, dynamic ports (62893) are outgoing; firewalls rarely block outgoing traffic, especially to localhost.
Tools to Spy on Your Computer’s Self-Chats
Want to see 127.0.0.1:62893 in action? These tools help:
netstat/ss(Command Line): The classics. Runnetstat -an | findstr 127.0.0.1(Windows) orss -tuln | grep 127.0.0.1(Linux/macOS) to see all active connections and listening ports involving localhost. You’ll see your server listening on a port (e.g.,127.0.0.1:3000) and clients connected from dynamic ports (e.g.,127.0.0.1:62893).- Resource Monitor (Windows): Visual tool showing network connections. Filter by “Local Address” containing
127.0.0.1. - Activity Monitor (macOS): Go to the “Network” tab. Look for
localhostor127.0.0.1in the addresses. - Wireshark (Advanced): The ultimate network sniffer. Capture on the “Loopback” interface and filter for
ip.addr == 127.0.0.1. You’ll see every single packet, including source and destination ports like62893and3000.
Why Understanding This Matters (Beyond Curiosity)
- Debugging Power: Recognizing
127.0.0.1:dynamic_portin logs instantly tells you it’s a local process connection, eliminating wasted time chasing phantom “external” threats or misconfigurations. - Security Awareness: Reinforces the concept of service binding (
127.0.0.1vs.0.0.0.0) and helps identify potentially suspicious local-only communication patterns. - Networking Fundamentals: Grasping ports, IP addresses (especially loopback), and client/server roles is foundational for any IT, development, or security role.
- Cloud & Container Confidence: Understanding local networking is essential before tackling the complexities of cloud VPCs or container orchestration (Kubernetes networking builds upon these core concepts).
FAQs: Your 127.0.0.1:62893 Questions Answered
- Q: Is
127.0.0.1:62893dangerous or a sign of hacking?- A: Almost certainly no. It’s overwhelmingly the sign of a perfectly normal, temporary connection between two processes on your own computer, like your browser talking to your local development server. Panic not!
- Q: Can other people on my network see or access
127.0.0.1:62893?- A: No.
127.0.0.1is the loopback address. Traffic to this address never leaves your computer’s network interface card (NIC). It’s strictly internal. The port number62893is irrelevant externally.
- A: No.
- Q: Why is the port number so random and big (like 62893)?
- A: Your operating system deliberately chooses unused ports from the high range (49152-65535) for temporary client connections. This “dynamic” assignment prevents conflicts. It’s random because the OS grabs the next available port when an application needs one.
- Q: I keep getting “Port already in use” errors. How do I fix it?
- A: This usually means the specific port (e.g.,
3000) you’re trying to use on127.0.0.1is already occupied. Solutions: 1) Find and stop the process using that port (via Task Manager, Activity Monitor, orlsof -i :3000/netstat -ano | findstr :3000). 2) Change your application’s configuration to use a different port. 3) Sometimes, simply waiting a minute allows the OS to fully release the port after the previous process exits.
- A: This usually means the specific port (e.g.,
- Q: As a regular user (not a developer), will I ever see this?
- A: Less frequently, but yes. Some background system processes, updaters, or even certain user applications might use localhost communication. You might glimpse it in detailed system logs or advanced task managers. Seeing it doesn’t imply a problem.
- Q: Is
localhostexactly the same as127.0.0.1?- A: For all practical purposes, yes.
localhostis a hostname that almost always resolves directly to the IP address127.0.0.1. They are interchangeable in most contexts. Technically,localhostcould be mapped elsewhere in the hosts file, but this is extremely rare and usually problematic.
- A: For all practical purposes, yes.
- Q: Can I choose my own dynamic port?
- A: Generally, no. Dynamic ports are assigned automatically by the operating system to the client side of a connection. You configure the server port (e.g., telling your web server to use port
8000). The client (like your browser) gets its outgoing port (62893) assigned dynamically by the OS.
- A: Generally, no. Dynamic ports are assigned automatically by the operating system to the client side of a connection. You configure the server port (e.g., telling your web server to use port
The Takeaway: Embrace the Whisper
The next time you spot 127.0.0.1:62893 (or 54321, or 59901) flicker across your screen, don’t ignore it as noise. Smile. It’s a tiny testament to the complex, efficient symphony of communication happening constantly within your machine. It’s your web server handing off data to your browser, your script querying its database, your tools coordinating seamlessly in the background – all using the secure, internal loopback highway and the OS’s clever management of temporary meeting rooms (dynamic ports).
Understanding this isn’t just technical trivia; it’s foundational literacy for navigating the digital world. It empowers you to debug smarter, configure more securely, and appreciate the intricate dance happening inside the box on your desk. So, go ahead – fire up your local server, check those logs, and witness the essential, self-contained conversations that make modern computing tick. What local service conversation will you notice today?
YOU MAY ALSO LIKE: welcome post on gravityinternet.net: Fast, Affordable Internet for All